Infrastructure Topics
Ransomware, phishing, and data breaches are omnipresent. However, who protects an organization from these attacks?
Security Administrators in the IT Infrastructure team, or Blue Team, do that!
The Blue Team protects IT infrastructure, systems, networks, and data. Blue Team security administrators must know firewalls, intrusion detection, and network protocols. Focus on Detail Small mistakes can lead to huge problems, therefore they monitor systems, analyze alerts, and secure the company's data and IT systems. They find and fix system vulnerabilities before attackers do. Security policies and ISO 27001 and GDPR standards are followed.
Ever wonder who protects your firm against ransomware, phishing, and data breaches in the exhilarating battlefield of cybersecurity?
Meet the Security Analyst and Administrator of the powerful Blue Team IT Infrastructure team! This movie shows their vital job, everyday activities, and why their expertise is essential for business security. Blue Team is your cyber knights, proactively using security tools to defend against threats. The Blue Team constantly detects, prevents, and responds to genuine attacks, unlike the 'Red Team' that simulates them for testing. Security analysts/administrators are crucial. They use Splunk to monitor activities, respond quickly to threats, manage vulnerabilities, enforce essential policies, and educate staff about cyber security. No matter how strong an organization's cyber security, data breaches and cyberattacks are always a threat. In the digital age, attackers exploit new weaknesses and find new ways to defeat even the most advanced security systems.
This is happening why?
Because the threat landscape is shifting quicker than ever. AI is used to launch targeted phishing operations, ransomware attacks, and zero-day vulnerabilities—software vulnerabilities that developers are unaware of. Every system has flaws, even with the best technology. Every defense has limits. Hackers just need one success, but defenders must always remain attentive. That's why organizations prioritize prevention, detection, response, and recovery. Not merely stopping attacks, but decreasing their impact. When an organization is targeted is the question in this high-stakes game of cat and mouse. Making sure an attack is discovered immediately, confined, and ended with minimal harm is crucial. We can prepare, adapt, and stay ahead of cyber risks, but not remove them. Every step we take in cybersecurity enhances our defenses for future battles.
That's IT Infrastructure Security Administrator life! These unsung warriors protect businesses from cyberattacks. If you liked this video, subscribe to the channel, and share it with an IT career seeker.
Infrastructure overview topology (Simple)
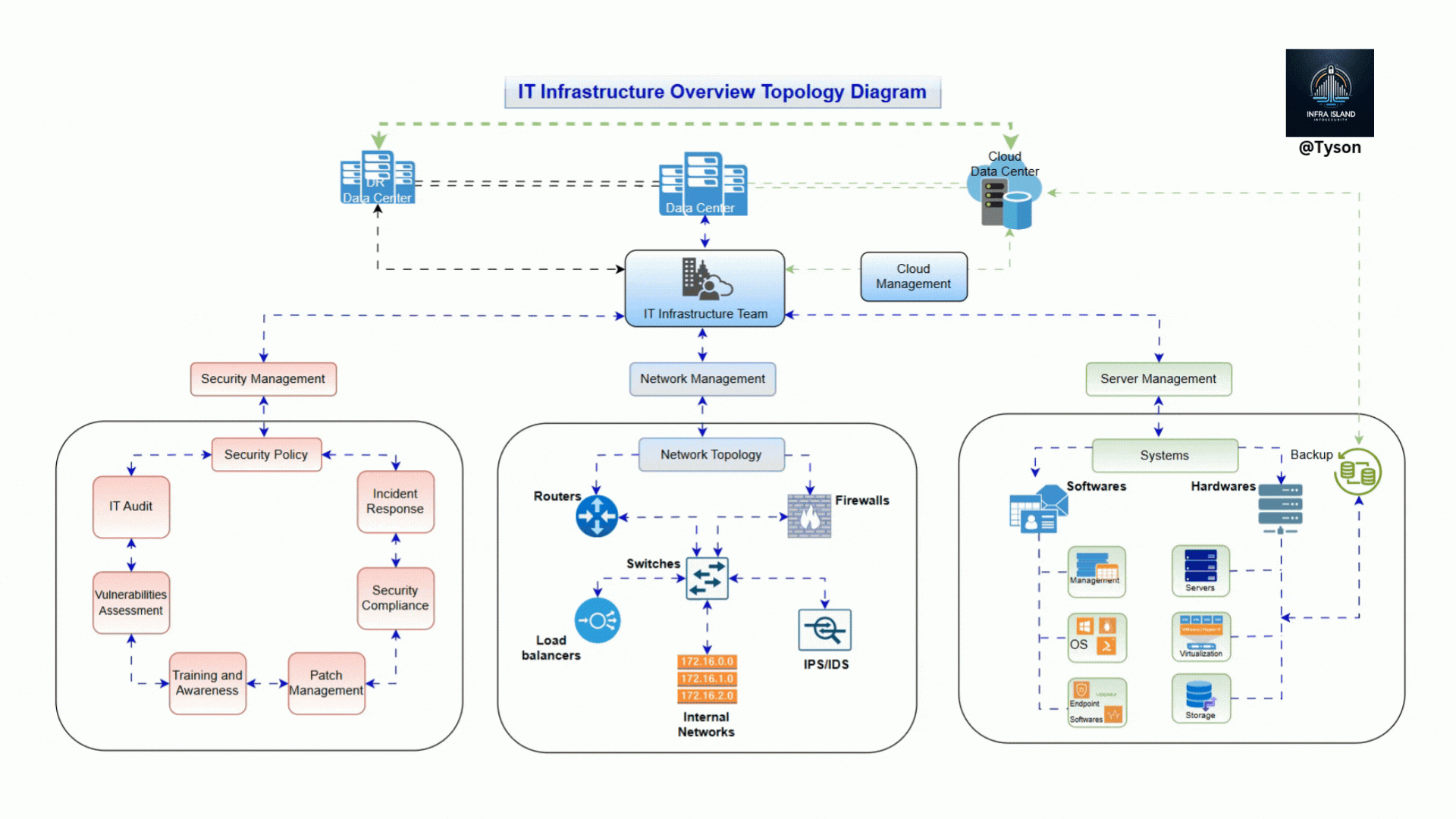
Essential Infrastructure Key Components

1️⃣ Systems Infrastructure
- Managing Windows Server & Linux Environments
- Active Directory Best Practices
- Virtualization with VMware and Hyper-V

2️⃣ Network Infrastructure
- Configuring Cisco Routers & Switches
- Understanding BGP, OSPF, and MPLS
- Setting Up VPNs for Secure Remote Access

3️⃣ Cloud Infrastructure
- Deploying and Managing AWS and Azure
- Hybrid Cloud Strategies for Enterprises
- Automating Cloud Deployments with Terraform

4️⃣ Security Infrastructure
- Implementing Zero Trust Security Models
- Hardening Network Firewalls (Cisco ASA, Palo Alto, FortiGate)
- Vulnerability Management with Nessus & IBM QRadar

Resources & Tools
🔹 Monitoring & Security Tools – SolarWind, PRTG, Nessus, IBM QRadar, ClearPass, NinjaOne
🔹 Cloud & Automation – Terraform, Ansible, Python Scripting
🔹 Networking & Firewalls – Cisco ASA, Palo Alto, FortiGate, CheckPoint
© Copyright. All rights reserved.
We need your consent to load the translations
We use a third-party service to translate the website content that may collect data about your activity. Please review the details in the privacy policy and accept the service to view the translations.